-
Device Segmentation
We deliver tailored Network & Device Segmentation Solutions that fits your company security
Overview
We deliver device segmentation solutions that enhance network security and performance by isolating sensitive assets. With advanced segmentation policies and tailored network configurations, our approach helps reduce attack surfaces and enables controlled, compliant access across your infrastructure.
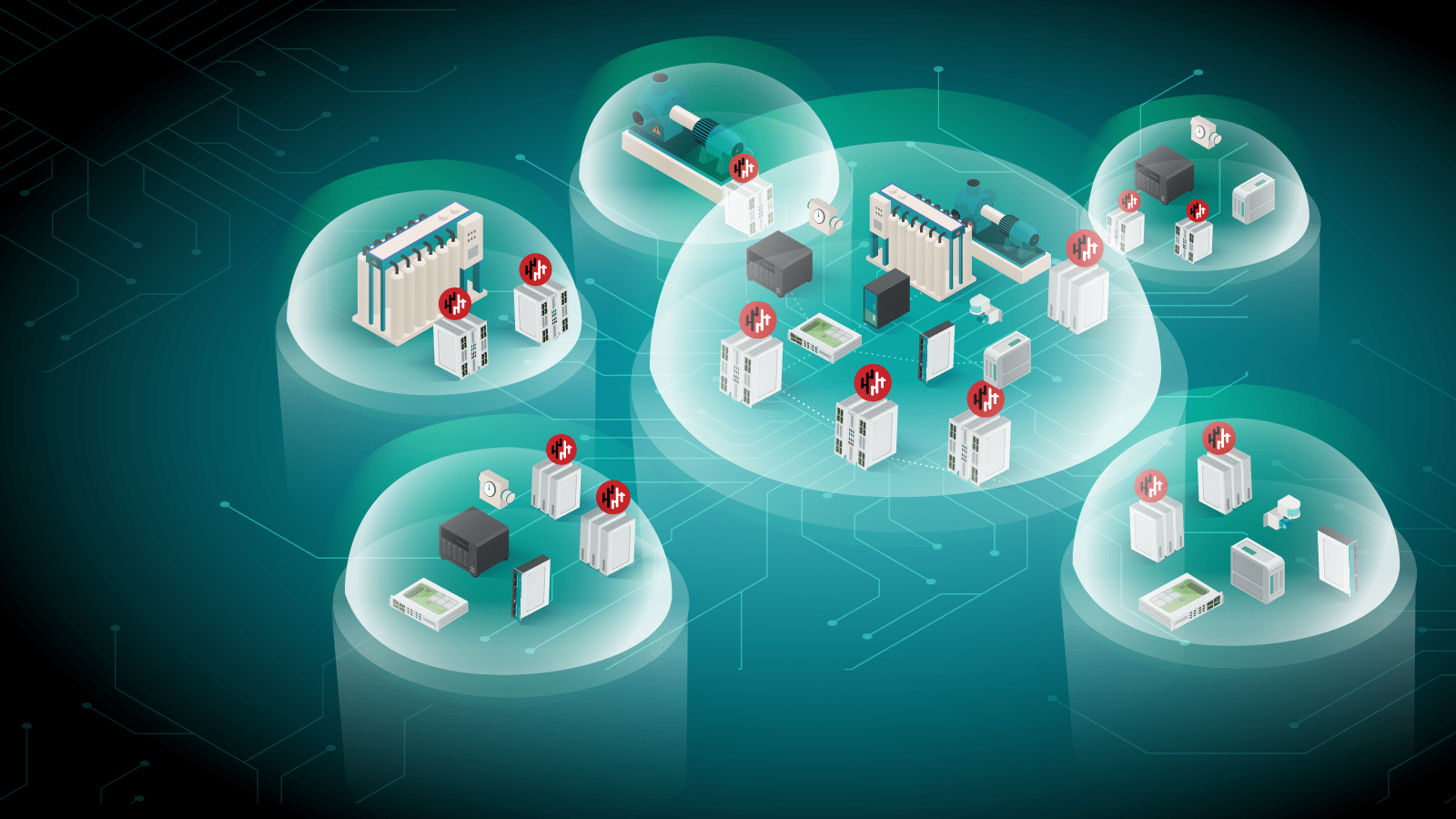
Solutions We Offer
🗸 Network Assessment & Planning: Evaluate your network to design optimal segmentation strategies, ensuring secure device isolation.
🗸 Customized Segmentation Solutions: Implement tailored segmentation to restrict access and minimize risk across devices and departments.
🗸 Access Control & Permissions: Establish robust access controls for segmented networks, limiting access to critical areas.
🗸 Monitoring & Support: Continuously monitor segmented networks to ensure security and quickly address any issues.
Key Benefits:
🗸 Reduced Attack Surface: Segment networks using Software-Defined Networking (SDN) or Cisco TrustSec to contain and isolate potential threats.
🗸 Access Control: Implement Network Access Control (NAC) systems such as Cisco ISE for secure and controlled device access.
🗸 Improved Network Performance: Use VLANs and micro-segmentation for optimized network traffic flow.
🗸 Compliance Management: Ensure compliance with frameworks like PCI-DSS and HIPAA by restricting access to sensitive data.

Technology Stack we use :



Additional Services We Provide

Business Analytics
Our business analytics solutions transform your data into strategic assets with actionable insights. Tailored to your specific KPIs in your organization.
Learn More→
Cloud Storage
We offer cloud storage solutions that are scalable, secure, and adaptable to growing data needs. Leveraging encrypted storage and flexibility based on the needs of your organization.
Learn More→
Vulnerability Management
We provide vulnerability management solutions that identify, prioritize, and address risks before they impact your operations and strengthen your cybersecurity posture.
Learn More→
Securing AI Models
Our AI security solutions safeguard machine learning models against adversarial threats and data vulnerabilities ensuring trustworthy AI-driven insights.
Learn More→

